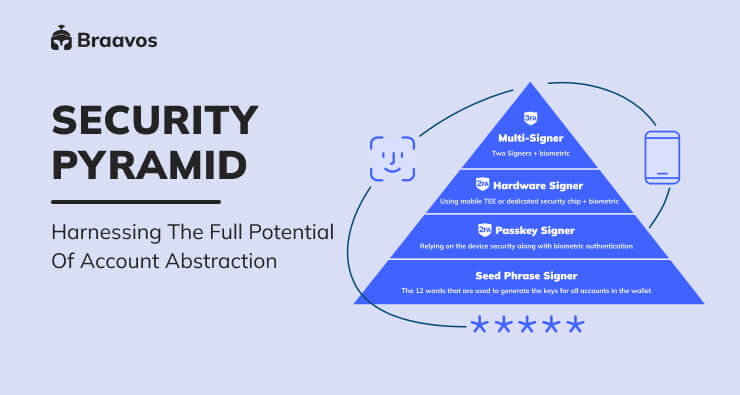
Account Abstraction Security Pyramid
2024 Update - The combination of great UX and top security is coming to the browser extension wallet as well with the new Passkey Signer!
At Braavos, we believe that security should be evaluated not only by its capacity to resist attacks but also by its ease of adoption and the extent to which it protects users from their own mistakes.
Regrettably, in the world of truly decentralized and self-custodial crypto, there hasn’t been sufficient emphasis on providing a user-friendly onboarding experience. Generally speaking, current products are quite unforgiving when it comes to user errors. A single mistake can result in the permanent loss of funds with no chance of recovery.
Most individuals who have engaged with crypto would concur that the user experience still has much room for improvement. The current crypto landscape is overly complex, placing a substantial burden on users and demanding that they grasp myriad highly technical concepts.
This is why many have turned to centralized platforms like FTX, Celsius, and BlockFi. However, as we all know, these solutions sometimes encounter issues or fail, leaving users without access to their funds.
It’s important to recognize that this isn’t the users’ fault. Instead, it’s the responsibility of the industry to provide more user-friendly and intuitive alternatives. To achieve this, we must substantially enhance self-custody and decentralized options, placing a strong emphasis on improving the overall user experience.
However, the focus on decentralization, which we value greatly, presents significant challenges. In contrast to the traditional web2 world, where relying on a centralized server can enhance the user experience, the decentralized world demands that we work harder and develop new, innovative approaches to provide a good UX.
Authentication Types
Before discussing how Braavos is working to improve users’ security and overall UX, it is important to first address security and authentication in general.
There are 3 main types of authentication:
- Something you know – a text password, PIN code, pattern, etc.
- Something you have – a physical device, such as your mobile phone or a YubiKey
- Something you are – a biometric identity, such as your fingerprint, face ID, retina, etc.
A robust security system typically combines at least two of the aforementioned types of authentication. Furthermore, the general trend in the broader technology and security industry is to move away from text passwords and PIN codes, since they are considered to be the easiest to compromise.
In crypto, we rely solely on “something you know” in the form of a mnemonic seed phrase, which is considered the weakest type of authentication.
We can do better!
In order to solve these problems and provide better security and UX, we leverage Starknet native account abstraction and cheap computation.
Starknet is a Validity layer-2 Rollup on top of the Ethereum blockchain (sometimes also called a ZK Rollup).
Starknet has two key characteristics:
- Scalable computation, which allows us to do things that are not economically viable on L1, taking advantage of the very low compute cost on Starknet.
- Account abstraction, which allows us to run customized signature verification logic and arbitrary execution logic on the transaction before it interacts with other contracts on the blockchain. Account abstraction is at the core of Smart Contract Wallets. One can think of accounts in such wallets as having two sides – the application side, which is responsible for presenting information to the user and signing transactions, and the contract side, which is responsible for verifying the transaction signature and calling the relevant contract(s) in order to execute it on-chain..
You can read more in our article about account abstraction.
This opens the door to a whole new design space and cool new concepts like the Account Abstraction Security Pyramid.
Account Abstraction Security Pyramid
The Account Abstraction Security Pyramid is a hierarchy of security measures that users can choose from to protect their accounts.
Seed Signer
At the bottom of the hierarchy, we have the Seed Signer, which derives its keys from the 12-word mnemonic seed phrase used to generate all accounts’ keys for a wallet. This is a widely recognized insecure method as it often exposes users to phishing attacks, malicious software attacks, and forgotten phrases, among other things.
Despite being based on the weakest form of security, namely “something you know,” a Seed Signer is still the prevalent method used in self-custodial wallets to secure funds.
Passkey Signer
The Passkey Signer, which is available to Braavos Wallet browser extension users, represents a significant leap in secure digital transactions. Leveraging the highest level of security available on your device, this feature typically utilizes a dedicated security chip along with biometric authentication—such as fingerprint or face ID. However, in situations where biometric ID is not available or feasible, the Passkey Signer can alternatively use your screen-lock password. This flexibility ensures that, regardless of the method, your account gains a substantial boost in security without compromising the ease-of-use.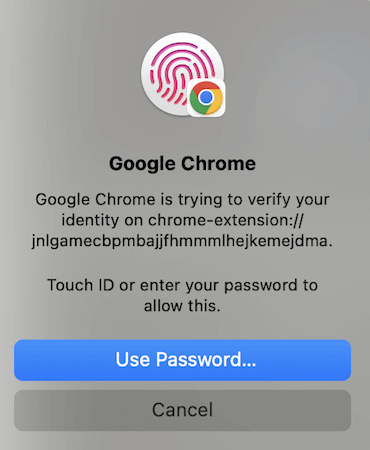
The Passkey mirrors the stringent security measures of the Hardware Signer, adapted for the browser environment. By integrating state-of-the-art Passkey capabilities of modern operating systems and browsers, the Passkey Signer effectively shields users from phishing attacks and other malicious activities, ensuring the utmost safety for your funds.
The two-factor authentication (2FA) mechanism it employs combines ‘something you have’ — your computer – with ‘something you are’ — your unique biometric identity, thus providing a seamless yet highly secure user experience for managing digital assets.
However, modern OSes and browsers support syncing passkeys with the cloud. This greatly increases convenience with the price of having your keys encrypted and sent to the cloud.
For enhanced security, you can disable it in your Chrome settings. For example, you can disable the option to ‘Use Passkey across your Apple devices’.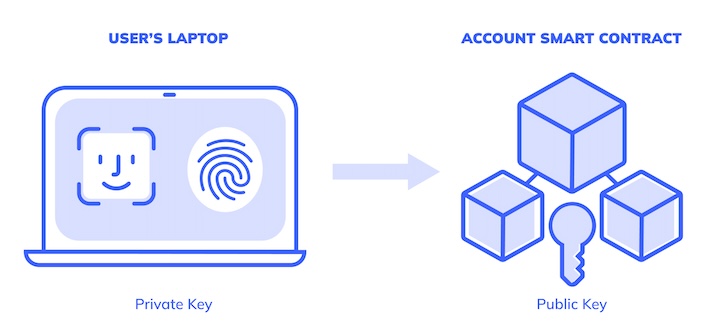
Hardware Signer
The next level in the pyramid is the Hardware Signer. The Hardware Signer utilizes mobile devices’ built-in security mechanisms in order to generate keys, authenticate the user with biometric ID and sign transactions.
There are 2 classes of security for the Hardware Signer:
- Protected Signer, also known as Hardware Signer TEE – uses a special secure mode of the mobile processor
- Hardware Signer – uses a dedicated isolated chip and presents the strongest level of device security mechanism
Both classes enforce 2-factor authentication (2FA), something you have (your mobile device) and something you are (your biometric ID). The Braavos wallet application will automatically choose the highest level of security available on the user’s device.
Protected Signer
The Protected Signer uses the Trusted Execution Environment (TEE) that is built into Android mobile devices, usually the ARM TrustZone.
The TEE provides a secure mode of the application processor. It divides the SoC into two virtual worlds – the normal world where all applications are running, and the secure world where only trusted applications can run.
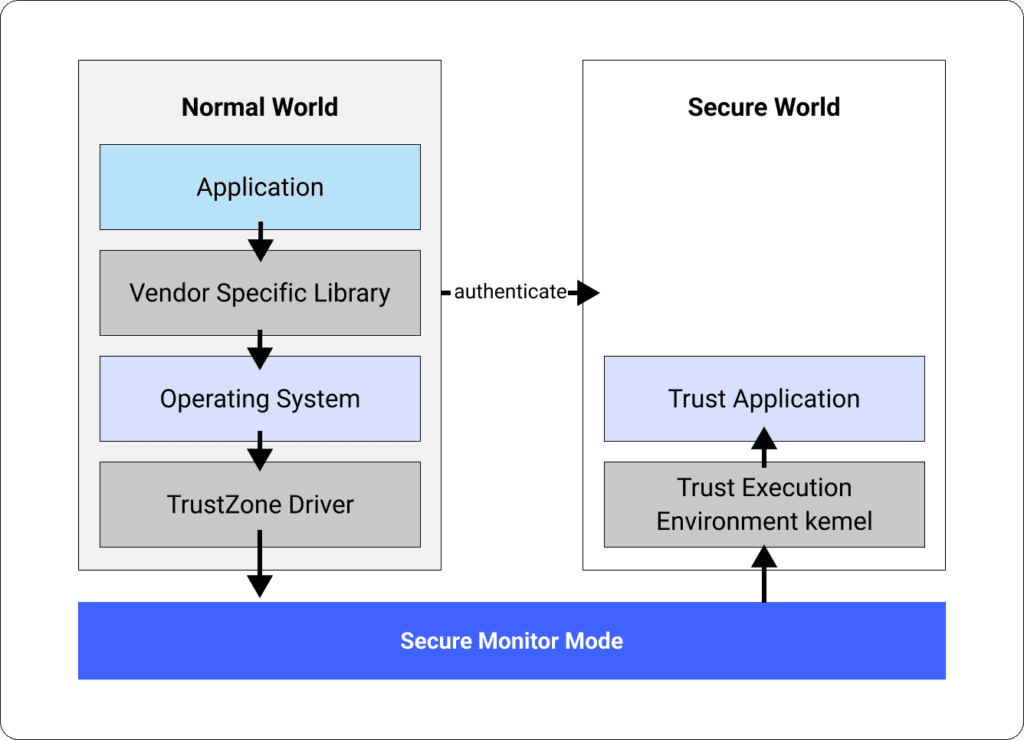
This means that operations like generating keys, storing keys, biometric authentication and signing transactions are isolated and are not accessible to applications in the Normal World.
This guarantees that no one has access to the private keys and that the signing process, approved by biometric authentication, is done without interference from outside parties.
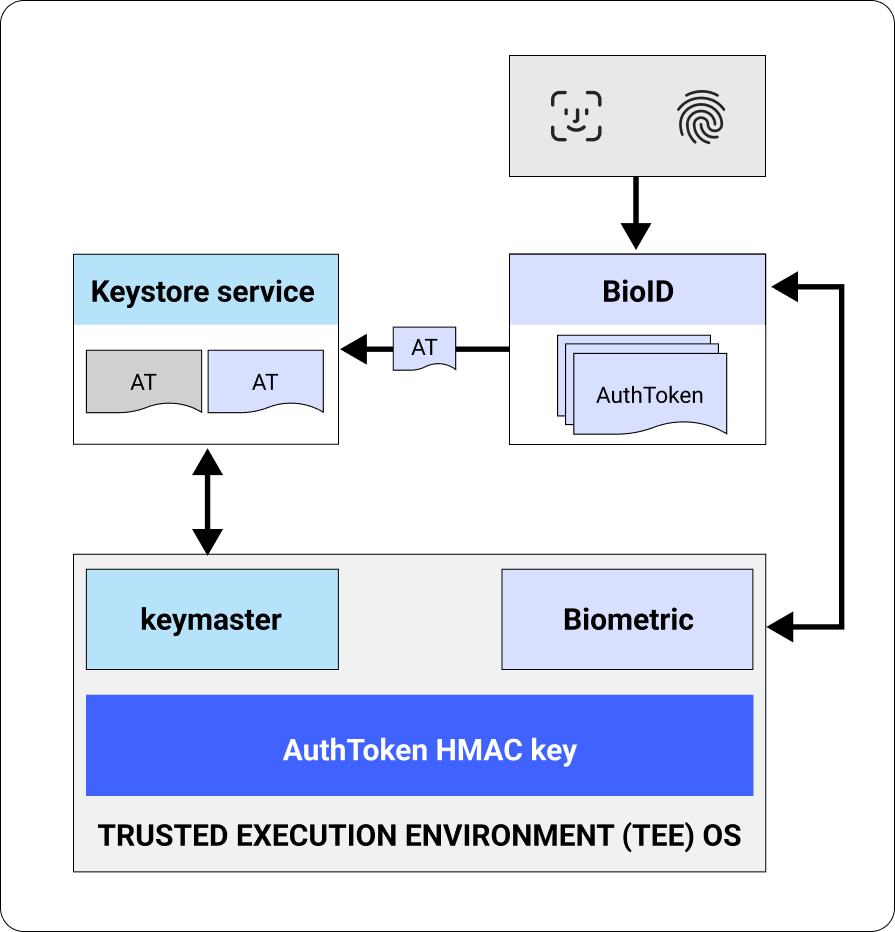
Supporting key generation and signing via secured biometric authentication means that we have two-factor authentication:
- Something you have (your mobile device), as the key cannot be extracted from the TEE and is unknown to anyone.
- Something you are (your biometric identity), which the TEE uses to approve signing transactions.

Hardware Signer
The Hardware Signer has a similar high-level functionality as the Protected Signer, but under the hood it uses a much stronger hardware to secure keys and sign transactions.
Starting with the iPhone 5S, all iPhone devices support a built-in Hardware Security Chip (HSM) – the Secure Enclave. Additionally, the latest Android devices, such as Google Pixel 3 onwards and the latest Samsung models, support a built-in HSM – the Titan M2 (in the case of Google).
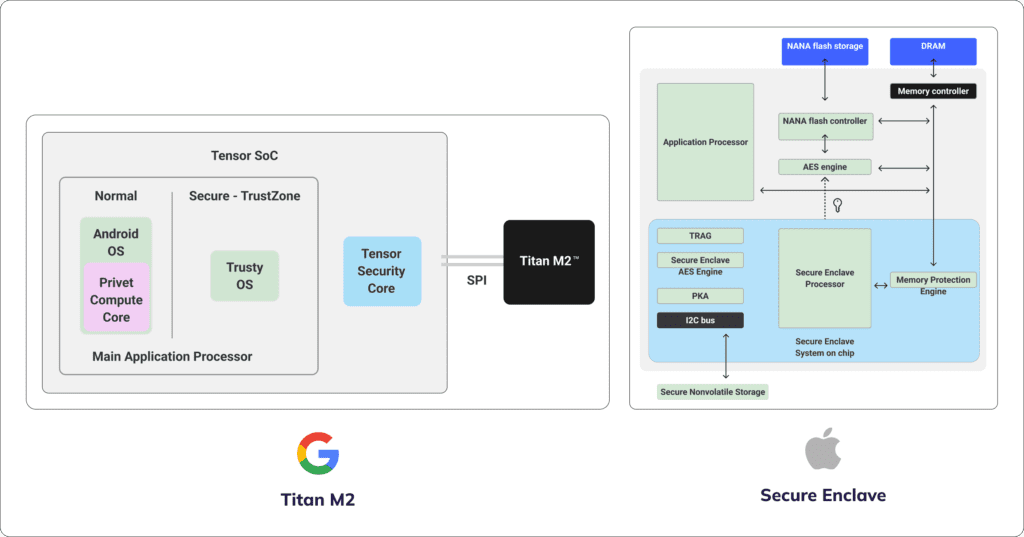
The Secure Enclave / Titan chip is a dedicated and isolated sub-system. Unlike the ARM TrustZone (used by the Protected Signer), which uses a virtual separation, the HSM is physically separated from the application processor.
- It can generate private keys and sign messages.
- It generates the keys using an internal True Random Number Generator (TRNG) and signs messages over the NIST-P256 elliptic curve (secp256r1) via its internal Public Key Accelerator (PKA).
- The private keys never leave the secure system and are unknown and inaccessible to anyone, not even to the user, or to the application itself.
This means that even if the device application processor kernel becomes compromised, user keys stay safe.
Using a Hardware Signer with a built-in HSM in a mobile device offers several advantages.
First, it provides an added layer of physical security, as the HSM is a tamper-resistant hardware that is difficult to hack or manipulate.
Second, it enables more secure and efficient key management, as the HSM can securely store and generate cryptographic keys, and perform the cryptographic operations of signing and verifying without exposing the keys to the outside world.
Finally, it improves the user experience by enabling fast and convenient biometric authentication and minimizing the need for manual input of long passwords or phrases.
Similar to the Protected Signer, the Hardware Signer also offers 2-factor-authentication- something you have and something you are.
Here’s a more detailed explanation on the Hardware Signer and the Secure Enclave.
How do the Protected Signer and Hardware Signer work?
The wallet application checks whether the device supports an HSM chip, such as the Secure Enclave, or a TEE, such as ARM TrustZone. Based on this, the user will be prompted to enable the Hardware or Protected Signer.
Once the user decides to add a Hardware Signer or Protected Signer to a new or existing account, the HSM/TEE generates a dedicated key pair for the account. The private key never leaves the HSM/TEE, while the corresponding public key is set in the account contract to verify transaction signatures.
It is important to note that the signature scheme supported by the HSM/TEE is not the regular signature scheme used in major blockchains, including Bitcoin, Ethereum and Starknet. The elliptic curve used for signing is called NIST-P256 (or secp256r1), which means that the account contract must run customized logic not inherently supported by the blockchain to verify the transaction signature (made possible thanks to account abstraction).
Once the wallet sets the Hardware/Protected Signer, it becomes the main key of the account, meaning only it can sign transactions.
Do we still need the Seed Phrase? Yes. In case my device is lost, stolen, or bricked, I can use the seed phrase to sign a ‘Remove Hardware Signer Request’ transaction. This request will have a 4-day time delay before it is executed and the user regains control of the account. During these 4 days, the Hardware Signer will still be the only entity able to sign transactions.
This means that if the user’s seed phrase is stolen, they will have 4 days to transfer their funds to a new and secure wallet.
Multi-Signer
At the top of the pyramid, we have the Multi-Signer. The Multi-Signer combines the protection of the seed phrase on the browser extension and the Hardware Signer or Protected Signer using the mobile device.
Now two signatures from two different keys are needed in order to execute the transaction on chain. We get 3-Factor-authentication:
- Something you know – the key derived from your seed phrase on the extension
- Something you have – your mobile device
- Something you are – your fingerprint or face biometric identification
Note that although we added another Signer, we did not add another mnemonic seed phrase!

If you have questions or concerns about the hardware Signer or the Protected Signer, please visit the FAQs.
Advance Security, Simple UX
This article delves deep into the technical aspects of our innovative security measures to provide you with a comprehensive understanding of the system. However, we understand that for our users, security should be seamless and effortless. Therefore, we have encapsulated all the technical complexities of our product, allowing for a smooth and user-friendly experience that feels familiar even to those new to the crypto world.
The account abstraction security pyramid is at the forefront of our mission at Braavos. It sets a new standard for security and UX, as for the first time in crypto, we introduce true multi-factor authentication, a groundbreaking feature that revolutionizes crypto UX and opens doors for a new cohort of users to adopt self-custodial crypto solutions. Our users can easily choose a security level that suits them and their devices, ensuring complete peace of mind. Trust us to provide a top-notch experience that marries high-level security and a smooth user experience.
To get started, download the Braavos Smart Wallet on your preferred browser or mobile device today.