Hardware Signer: Enhancing Security of Crypto Wallets
Background
In the past few months we, at Braavos, have focused on implementing the basics users need from a self-custody wallet.
We released the wallet as a browser extension for all popular browsers and an application for iOS and Android devices. Users can access their funds wherever and whenever they want.
We introduced numerous features to the wallet, such as NFTs gallery for audio, video and 3D image.

Transaction Explainer that helps users understand in clear English what dApps are asking them to sign on.
Built-in Exchange so users can swap tokens from within the wallet at the best rates on StarkNet.

Mobile apps that are aligned with our vision for better security through better UX, superior to browser extensions.

All the above were completely new capabilities for StarkNet when Braavos introduced them, but other wallets in the wider crypto ecosystem have already implemented such capabilities.
Nevertheless, it was important to us to cover “the basics” and give users the functionality they are used to from L1 and other chains.
Once we have covered the basics, we have been directing all our efforts towards new innovations enabled by Account Abstraction coupled with L2 low gas fees. The goal is to improve the security and user experience of self-custodial wallets, ensuring people will not default to centralized solutions.
Common Ways to Secure Accounts
Today in crypto, there are two main ways to secure your account: a seed phrase or a hardware wallet.
Seed Phrases
A Seed Phrase is a 12 or 24 words users must store safely.
It presents a notorious UX as it’s subject to phishing attacks and frequently gets lost, resulting in users losing funds.
Hardware Wallet
A Hardware Wallet offers strong security, but presents very high friction for everyday users, as it is another physical device to handle, needs to be specially ordered, is costly, and users need to learn how to use it.
Is there a better way?
Hardware Signer
The Hardware Signer presents the first step in our journey to improve crypto user experience and make it much more accessible and secure for everyday users, while not compromising on decentralization and self custody.
So what is the Hardware Signer?
The Hardware Signer consists of two parts:
- The secure sub-system in users’ mobile device
- The account smart contract which can run arbitrary logic
(a.k.a Account Abstraction)
Secure Sub-System
The Hardware Signer utilizes the secure subsystem built-in in users’ device — iPhone’s Secure Enclave or Android Phone’s Titan HSM – to protect the account.
The Secure Enclave / Titan chip is a dedicated and isolated sub-system, totally separated from the application processor, that can generate private keys and sign messages. It generates the keys using an internal True Random Number Generator (TRNG) and signs messages over the NIST-P256 elliptic curve (secp256r1) via its internal Public Key Accelerator (PKA). The private keys never leave the secure system and are unknown and inaccessible to anyone, not even to the user, or to the application itself.
This means that even if the device application processor kernel becomes compromised, user keys stay safe!
Deeper into the Secure Enclave
During the chip manufacturing process, a UID (Unique Identifier) is generated by the TRNG and is stored in the PKA. It can’t be read and never leaves the PKA, thus it is unknown even to the Secure Enclave processor and the Secure Enclave Processor Operating System (SepOS).
This UID is a random number which is unique per device and is used to encrypt all other keys that will be generated in the future on this device.
The way it works is as follows: the application will request the SepOS to generate a new key-pair, the SepOS will instruct the Secure Enclave TRNG to generate a key and encrypt it (using the UID). The app can then request the SepOS to decrypt the key and sign a message using the generated key. During this entire process, the generated key does not leave the enclave and is unknown to anyone.
(For more information on the Secure Enclave, please see here).
The way the Secure Enclave is built and operates, along with the fact that it is a target for attacks by powerful corporations and governments around the world, is the reason its security surpasses standard hardware wallets.
Account Abstraction
The power of Braavos as a smart contract based wallet on top of StarkNet is that it is comprised of two pillars:
- The client side (e.g. the application) that allows the user to review/sign transactions and send them to the chain.
- The chain side — an account smart contract that can run arbitrary logic; and in our case, run arbitrary signature verification logic.
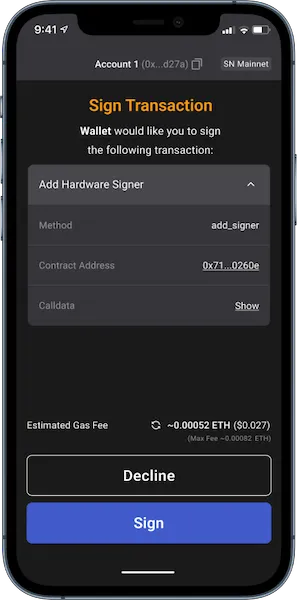
The application signs the transaction using the mobile device security module and then sends it to the account contract on-chain that can verify it.
As mentioned above, the security module on iPhones and Android phones uses a cryptography called NIST-P256 (secp256r1), which is not compatible with any major blockchain cryptographic scheme, including StarkNet.
This is why having a smart contract account on-chain that all transactions go through and can run arbitrary logic is crucial in utilizing these hardware secure modules on iPhones and Android phones.
Biometrics
How does the user approve the transaction?
Can a malicious application auto-sign a transaction without the user’s consent?
The answer is clear: NO!
The cool thing about the built-in security module in mobile devices, such as the Secure Enclave, is that it supports, intrinsically biometric authentication of the user identity.
This means that even the actual approval to sign a transaction is done directly versus the Secure Enclave. This means that the transaction approval, which is done via the user fingerprint or face identification, does not go through the application.
Recovery
If no one knows the private key, what happens if the device gets lost or becomes bricked? How can the user gain back control of the account?
In Braavos, when the user has enabled the Hardware Signer feature, an account will have 2 public keys:
- The Hardware Signer key that will be used to sign all transactions
- The key derived from the seed phrase that can only sign one transaction — a “Request to remove Hardware Signer”
This request to remove the Hardware Signer won’t be executed immediately, but rather will have a time delay of 4 days (configurable). This delay allows the user to use the Hardware Signer to cancel such a request.
This means that if the device gets stolen, lost or bricked, users will still be able to recover their account once the 4 days delay period ends.
However, if their Seed Phrase gets stolen and an attacker issues a request to remove the Hardware Signer, the user will automatically (and repeatedly) get notified and will be able to cancel the request and keep all of the assets safe.

Summary
The Hardware Signer feature offers both state-of-the-art security level for crypto users and the experience users are used to from web2 solutions. In this sense, signing a transaction is as smooth and worry free as paying with Apple/Google pay.
This is just one, yet prominent, example of the power of smart contract based wallet (a.k.a Account Abstraction) and the new design space it enables.
We foresee the development of more and more nascent capabilities that will drive the crypto industry to a better and more inclusive future, providing new and existing users alike with uncompromised security coupled with uncompromised UX.
The Braavos wallet is available on Android and iOS and on multiple browsers: Chrome, Firefox, and more.
Motty Lavie, founder and CEO at Braavos.
Twitter @mottylen