How To Crack the Crypto Seed Phrase Problem
Crypto seed phrases are easy to forget - and easy to exploit. Users deserve better, and account abstraction provides a way.
Braavos CEO Motty Lavie recently appeared on the Stark Cafe, a Twitterspace hosted by crypto commentator Nurstar, to discuss seed phrases and other aspects of crypto security. This is an adaptation of his comments.
There are three main types of authentication. There’s something you know, which is usually a password or a PIN code or a pattern. Something you have, which is a physical device. And something you are, which relates to your biometric identity. It could be your fingerprint, your face, or your retina.
A good form of authentication is based on at least two of these three, and preferably not something you know, because it is considered to be the weakest one.
And yet in the Crypto industry, we mainly rely on something you know – the notorious 12-word seed phrase, is the primary means of protecting and recovering our wallet.
Now, let’s start by putting ourselves in the mind of a crypto attacker. Specifically, what an attacker needs to do to compromise your account.
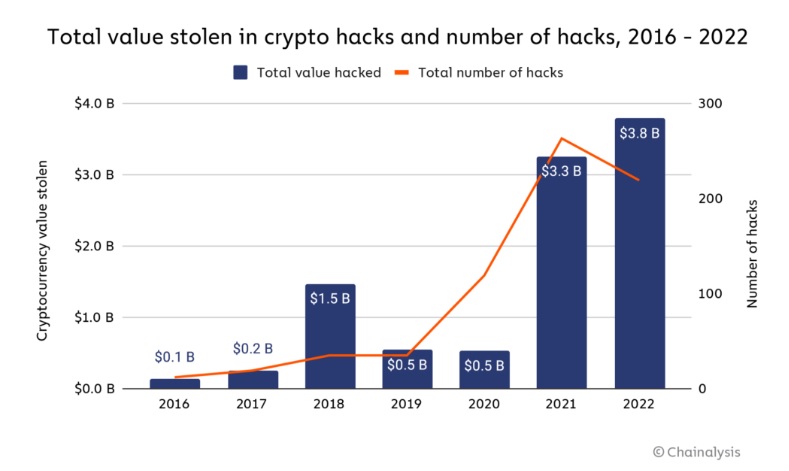
Currently, the only thing an attacker needs to do is to steal this 12-word seed phrase. And we are all familiar with phishing attacks and malicious software, which can easily steal these disparate words if you keep them on your hard drive.
Add to that the fact that any wallet vendor – either by mistake, or malicious intent, or under duress from a regulator – can make your wallet fully custodial in one update. That’s not a good combination.
But there’s an answer to crypto’s seed phrase problem.
And it’s sitting right there, in your pocket.
Today, all mobile devices come with a built-in security chip. This is very powerful.
- It’s capable of generating hardware keys that are bound to your device, isolated from the outside environment and unknown to anyone (even to you).
- It’s capable of performing biometric authentication before allowing these keys to sign transactions.
We can deploy this capability, and adjust it to the blockchain, using the power of account abstraction, a blockchain feature that allows us to treat accounts as smart contracts and enable us to provide more flexible wallet options. Specifically, it allows us to perform custom signature validation.
Your smart contract account, which is on-chain, can easily “talk” to the security chip, which is on your mobile. They “talk” in the same security language. They can sign and verify the same elliptic curve.
Harnessing both of these together brings the extremely strong security of two-factor authentication.
That’s why we introduced the Braavos Hardware Signer.
The Hardware Signer is a great combination of high security and extremely good UX.
The idea behind the Hardware Signer is to provide two-factor authentication: something you have and something you are. In fact, it relies on the phones we carry around with us.
- The something you have is your mobile device.
- The something you are is your biometric identity, on your mobile.
So, if we put ourselves in the attacker’s shoes again, they’d have to physically steal your device and steal your biometric identity, like your face or your finger. It’s possible, but an order of magnitude more difficult than stealing your crypto seed phrase.
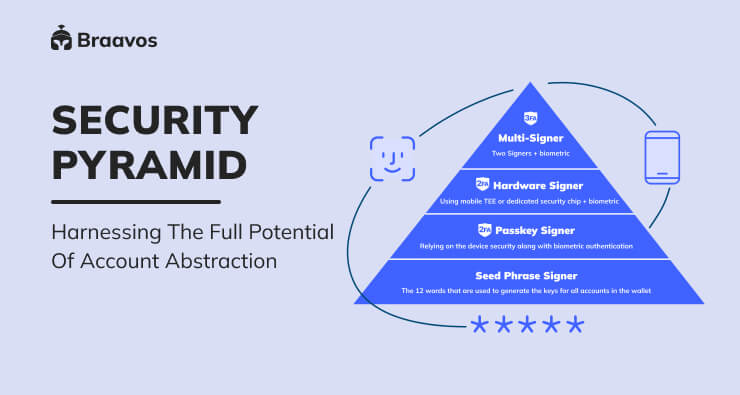
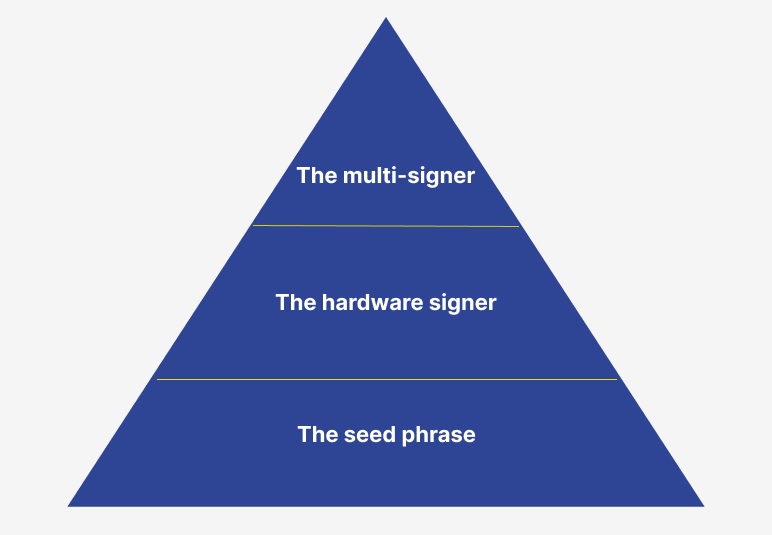
However, we do still use seed phrases at Braavos. In fact, we use them to provide a third authentication factor to create a Multi-Signer.
If you sign on your laptop or desktop computer in addition to your Braavos mobile app, you get 3FA: the seed phrase as well as the Hardware Signer.
This allows you, as a user, to sign onto different devices before a transaction goes through and communicates with other contracts on-chain.
Only when all these three conditions are met will the transaction leave the account contract that is on the chain and actually be executed with other contracts.
So you have three layers of security, which we call the account abstraction pyramid. And the UX is similar to what you’ve already used with apps like Apple Pay.
But we know what you’re thinking: Doesn’t the key storage create issues?
One thing I hear a lot is: “I don’t feel right that Apple has access to my private key.”
But don’t worry: no-one has access to your private key.
Not Apple. Not the Apple operating system. Not the Braavos app. Not the phone vendor.
No-one has access to your keys because your keys are generated and stored in silicone.
This means that even if, tomorrow morning, a regulator comes to the phone vendor – Apple, Samsung, Android Pixel or however – and says ‘we want you to bring us the keys of the Nurstar phone, or you go to jail’, they cannot do that.
And that is very strong indeed.
If you want to download the Braavos wallet and experience the power of multi-factor authentication, download it here.